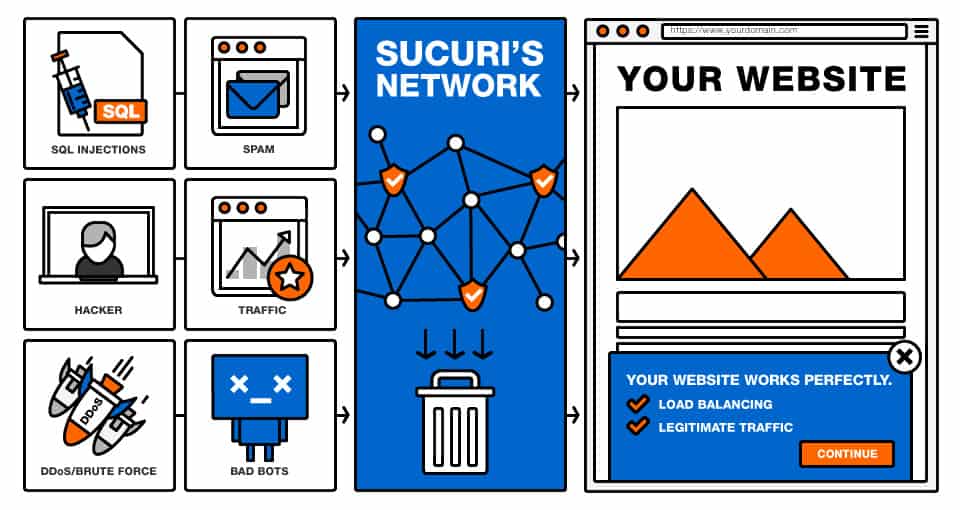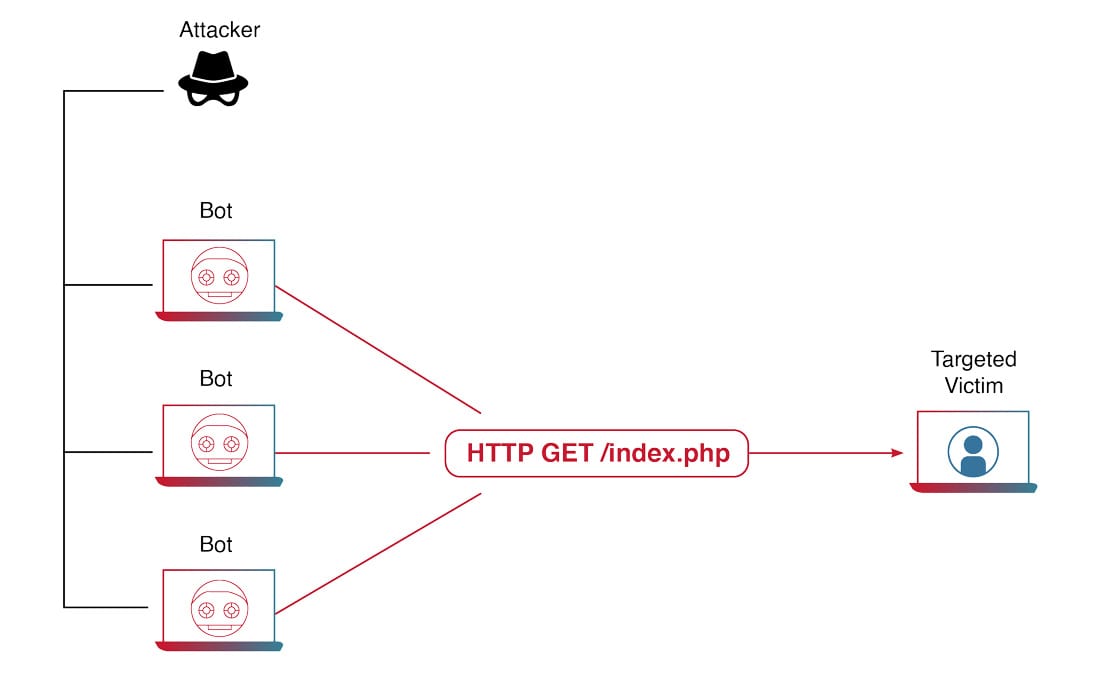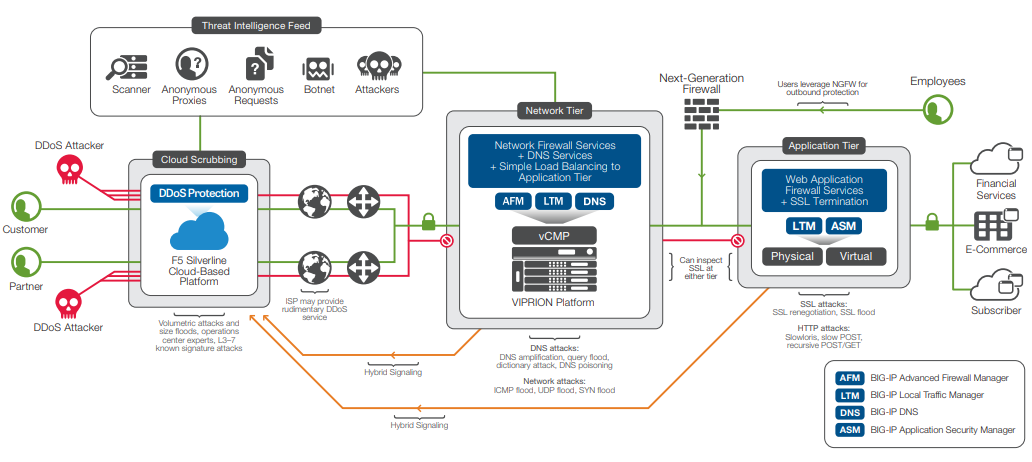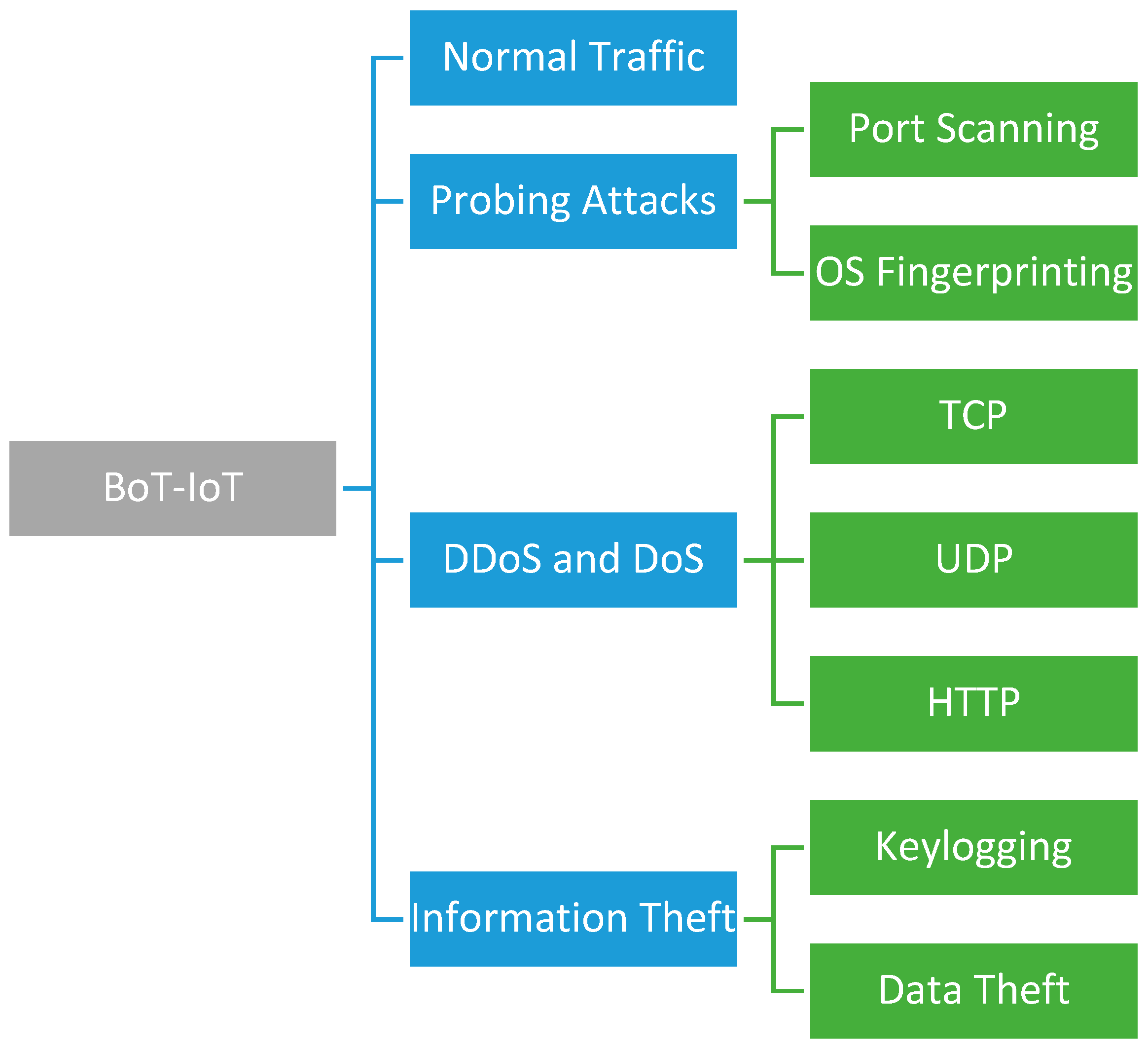
Applied Sciences | Free Full-Text | A Secure and Intelligent Software-Defined Networking Framework for Future Smart Cities to Prevent DDoS Attack
![PDF] Machine Learning Classification of Port Scanning and DDoS Attacks: A Comparative Analysis | Semantic Scholar PDF] Machine Learning Classification of Port Scanning and DDoS Attacks: A Comparative Analysis | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4c304cfa88cd53cddd7f5547d9728737aa0988c7/2-Figure1-1.png)
PDF] Machine Learning Classification of Port Scanning and DDoS Attacks: A Comparative Analysis | Semantic Scholar
GitHub - Malam-X/DragonMS: DragonMS is Tools for ddos, scanner, tracker, payload generator msfvenom and scraping
Cyber security concept line icons set. Pack outline pictograms of fingerprint scanner, spam, ddos phishing attack, danger, internet, scam, antivirus. Flat elements for mobile app and web design Stock Illustration | Adobe





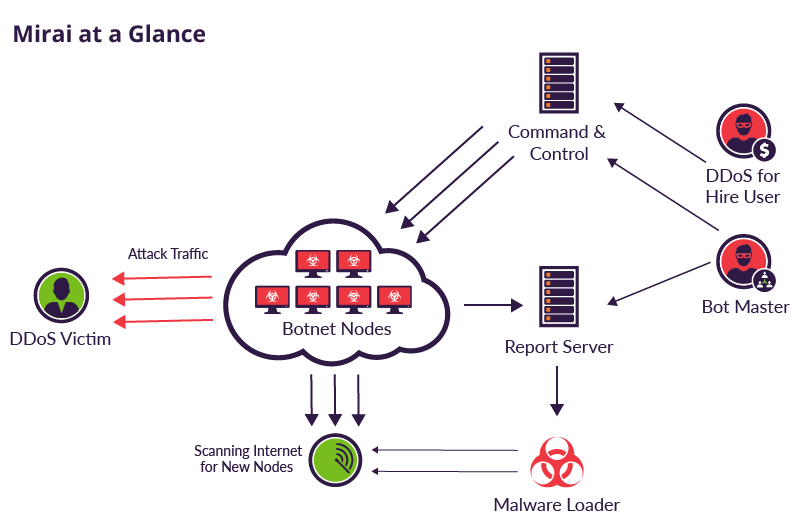



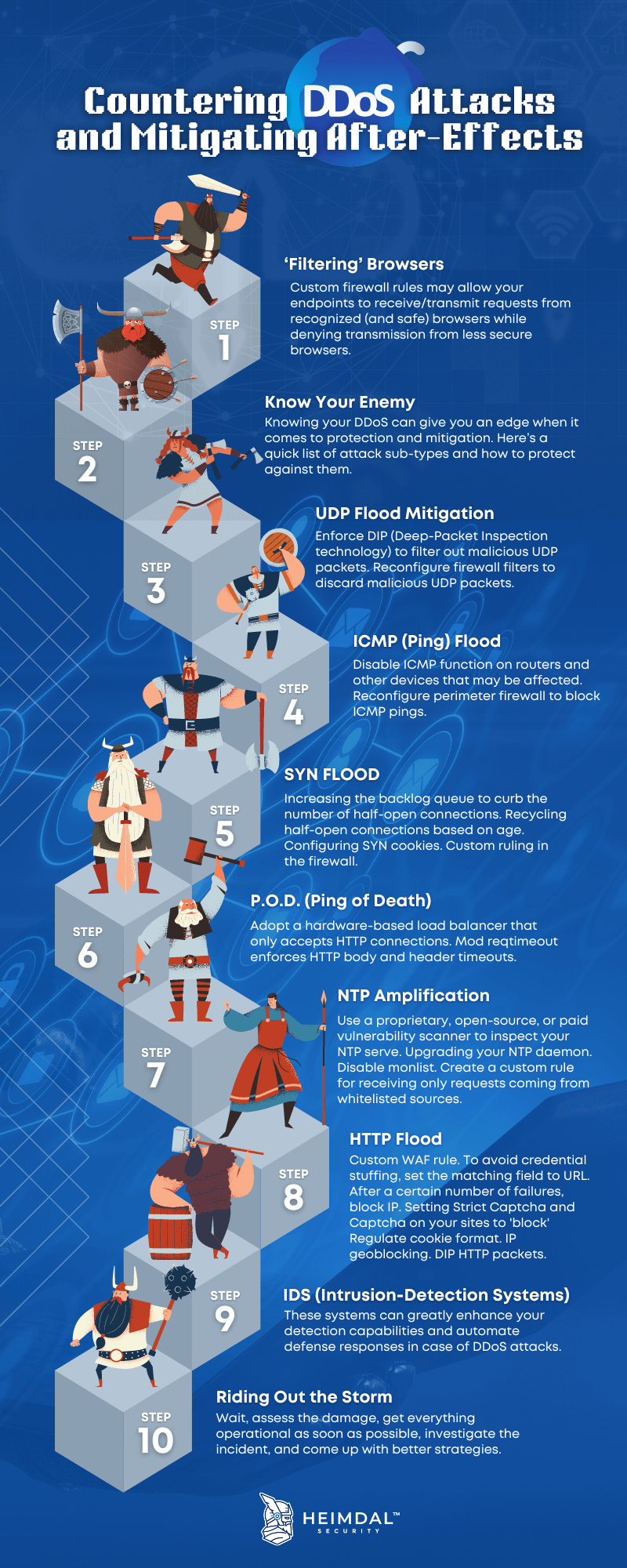
![PDF] A taxonomy of DDoS attack and DDoS defense mechanisms | Semantic Scholar PDF] A taxonomy of DDoS attack and DDoS defense mechanisms | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/fc99eaba660979d4e601fdbbb44e03b5fb9ea8d2/4-Figure1-1.png)